SSL Certificate Deployment in Active Directory Group Policy
Introduction
What exactly are Group policies and Group policies objects?
A Group policy is a function that allows organizational administrators to remotely control user and machine configurations in a domain leveraging a variety of policy baseline configurations/standards settings and preferences. We see this especially with organization with strong compliance requirements such as FedRAMP and CMMC 2.0. A Group Policy object (GPO) is a set of Group Policy settings linked to a specific Active Directory (AD) site, domain, or OU.
Examples of these security settings like password policies and account lockout policies, administrative templates, and more, are examples of Group Policies coupled with a GPO. These GPOs are where Group Policies are updated, and the modifications are carried forward to all objects to which the GPO is linked.
Group policies are a collection of security and management directives managed and updated to keep a network secure and running smoothly. For various reasons, these Group Policies may need to be revised immediately at times.
As a result, Microsoft has included tools to compel Group Policy upgrades. First, we’ll go over Group Policies in this post, then look at the default Group Policy update schedule, why you might need to force updates, and how to force Group Policy updates on a network.
Deployment With Active Directory Group Policy
Certificate Install Microsoft Group Policy 1
In many circumstances an organization will have a requirement to deploy various types of SSL certificates for servers, client devices, laptops, and workstations for organizations. Examples of this can be self signed certificates created on individual devices looking to get deployed throughout an organization.
In this example we're going to deploy a self signed certificate from our Microsoft Remote Routing and Access Server (RRAS) into the trusted root repositories for organization machines as part of a VPN solution.
This article picks up from the NicheITS knowledge base article: https://www.nicheits.com/knowledge-base/configure-certificates-iis/
We now need to extract the Remote Access server IIS Self-Signed Certificate as well.
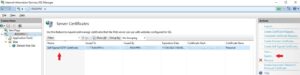
Goto the IIS manager -->on the left select the root of your server and go to the Server Certificates Icon.
You then want to select on your created Self Signed certificate and on the right select Export
The Export wizard will ask you to create a location to save and a password. A password is not required but is recommended.
Once Exported you will need to copy and paste this file over to the Domain Controller Group Policy Manager and import this into a GPO.
Certificate Install Microsoft Group Policy 2
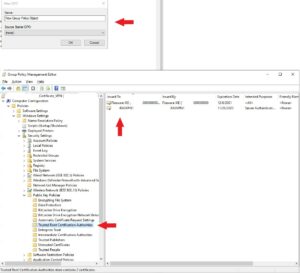
Once in Group Policy Manager you want to create a new GPO.
Provide a name such as, Example: "Domainname_Certificates_VPN_Deployment"
Goto: Computer Configuration --> Windows Settings -->Security Settings -->Public Key Policies --> Trusted Root Certification Authorities and import your RRAS IIS Self Signed Certificates.
Once correctly uploaded you will see the instances defined.
Deploy the GPO into the root domain or Organizational Unit (OU) you have defined that will require this certificate or certificates.
Administrators can now update this deployment throughout the organization with a group policy update with the command prompt use of "gpupdate /force" on individual machines.
References:
- https://learn.microsoft.com/en-us/powershell/module/grouppolicy/invoke-gpupdate?view=windowsserver2022-ps

